Welcome to integrity first corporations cyber security in October program. Week one, we’re going to talk about recognizing and reporting phishing.
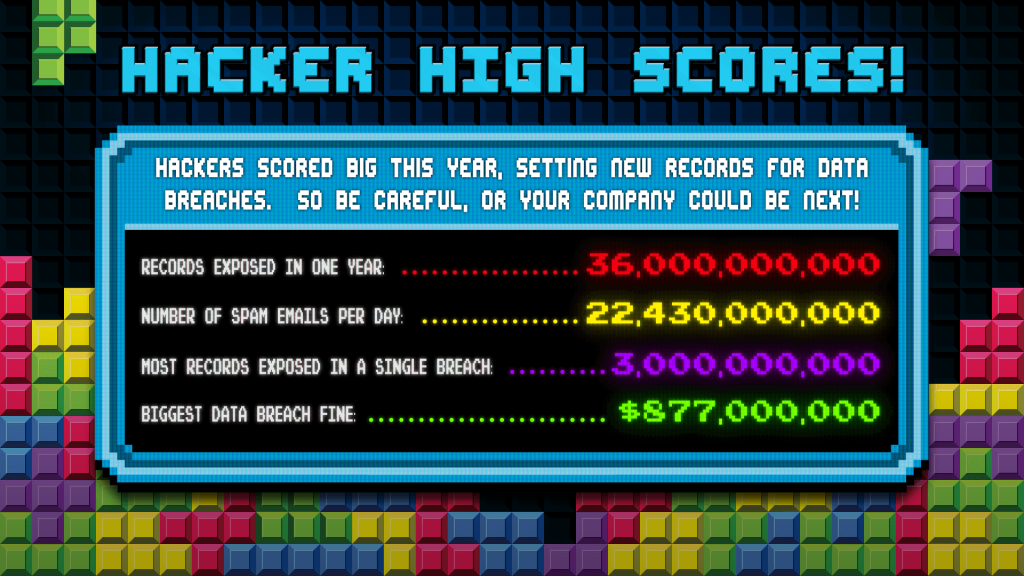
A few quick facts: cybercriminals sent over 3.3 billion phishing emails last year. This caused over 4000 data breaches then exposed over 22 billion personal records.
But it’s not enough to know that phishing emails are out there. You also need to be able to recognize them and report them.
So today, we’re just going to quickly review a few of the highly used phishing email types and tactics.
The first type is a reward or a free gift message. Free things are really enticing, but they can also be dangerous. If you get an email saying you won a free TV or click here to enter a prize drawing, you need to be on high alert. Hackers are definitely trying to bait you into clicking a malicious link.
The second type is a login or password message. Another type of phishing email will ask you to verify your account by logging into a fake web page or updating your credentials on this fake web page. These emails will collect your username and password which gives a hacker instant access to your account.
A third phishing email type is an urgent message. An urgent message email is designed to get you to act fast. It might tell you that your account was hacked or it’ll be deactivated; click here to restore it. Fear makes people do things without thinking, so slow down and make sure that this urgent message is from who you think it’s from.
The final type of common message is internal messages. This type of phishing is also called spoofing. Hackers will try to impersonate or spoof people at your company, like your HR rep, somebody in your IT department, or maybe even a co-worker. An internal phishing message email might ask you to click on a link to read and sign a policy, read a new document about company wide updates, or even handover sensitive information via purchase.
If you think you’ve encountered a phishing email, you need to follow your company’s procedures for recording it. Once the right people are notified, they can help you to determine if it’s a phishing email. Whatever you do, do not click on the links, don’t reply to the email and don’t send it to anyone else.
We’ll see you next week for Level Two.
