Did you know that, according to Pew Research, 39% of people use the same password for everything? Why is that bad? For example, Sony got hacked a few years ago, and what was really interesting was that the incidence of fraud didn’t just happen with Sony, but it went up at target.com and it went up at amazon.com. It went up kind of across the board, about 35 to 40%. And why is that? Because when one thing is hacked, the people that steal the data, actually take all of that information and try to use it online at as many places as they possibly can because they know that about a third of people use the same password for everything.
With that said, it’s really important to have a good password. And not only that, it’s important to have a different password for each account.
What constitutes a strong password?

A strong password is typically at least 12 characters, and it consists of uppercase letters, lowercase letters, numbers and symbols. Now, we know that’s going to be a little bit difficult to remember. So typically, we recommend using songs or other other things that are familiar with you to remember your passwords. For instance, say you are a Frank Sinatra fan. So, one of your passwords might use the phrase “fly me to the moon”, then adding a symbol and some numbers.
So, make sure that your passwords that you have to remember are something that’s easy for you to remember.
Using a password manager

The average American has over 120 passwords. Now, you can’t be expected to remember 120 passwords with 12 characters, uppercase letters, lowercase letters, numbers and symbols. One thing that we do recommend is a password manager. With a password manager, you only have to remember one password to get into the password manager, and then you can actually store all of your passwords within the password manager itself.
What’s really nice about a password manager is it will help you create passwords that are secure as well. When you create a new password, you actually would just click on new, and then it will fill in the password for you if you want it to.
Good password manager examples
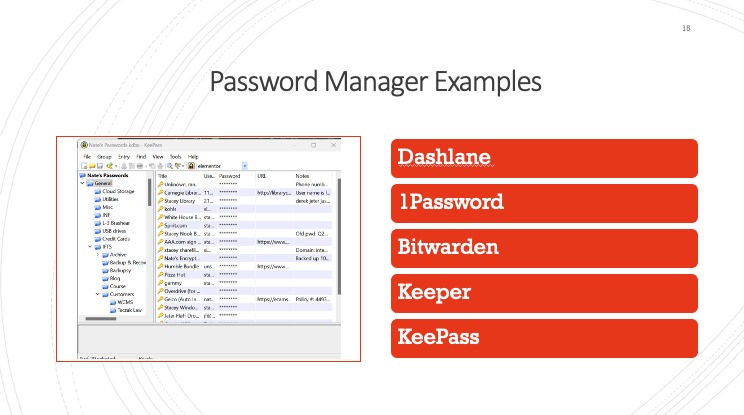
We’ve only put Password Manager examples on this list that have not been compromised in the commercial market. There are some other password managers on the market that have been compromised, so they didn’t make this list. Some examples are Dashlane, 1Password, Bitwarden, Keeper and KeePass. INF and Integrity First Technology Solutions both use KeePass.
You can see in the photo above, in a password manager you have your list of passwords, then you’ll have your username and your password. So let’s say you want to login to your bank. You will go to your bank’s website, you double click on your username, and then you click paste. And it would go right into the browser and then you would double click on the password, click paste, and then it would sign you in.
So you just have to remember that one password to open your password manager, and then you have access to all of your usernames and passwords.
Two Factor Authentication
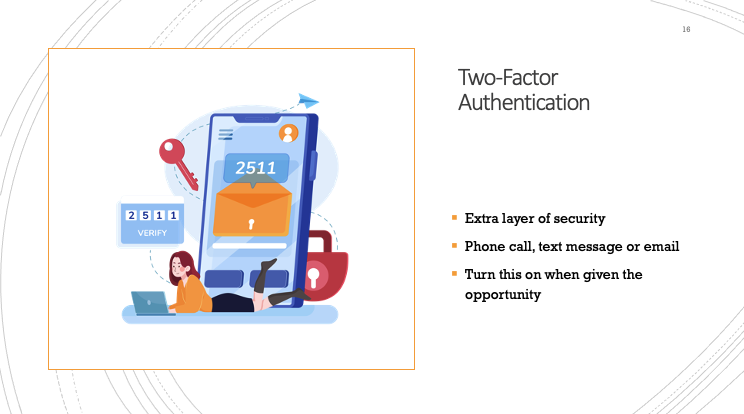
Another thing that goes along with passwords is two factor authentication, or you might have seen it as 2FA. Two factor authentication is an extra layer of security that actually would have helped all those people that had the same password for everything. So not only do you have to enter your username and password, but then there’s an extra step. This is most likely something that you have seen before. You’ll put in your username and password and then they’ll ask if you want to receive a phone call, a text message or an email with your one time verification code.
Once you choose your verification method, they will send you your verification code just like it’s shown in the picture above. You would put the verification code in and then you can sign in to your account.
We definitely recommend turning this on when you’re given the opportunity to do so, because it really is a very strong extra layer of protection, and it protects your accounts from hacks. If a company were to get hacked, they would get your username and password but they wouldn’t get access to your two factor authentication, they wouldn’t get access to your phone, or your email, so this would definitely help protect your account from any hack that happened.
The weakest link in the security chain
“Companies spend millions of dollars on firewalls, encryption and secure access devices and it’s money wasted. None of these measures address the weakest link in the security chain.” – Kevin Mitnick. What do you think is the weakest link in the security chain? If you said humans, you are correct!
Questions about anything in this article? Contact Stacey Ivol at 412-563-2106 or email her at sivol@integrityfirstins.biz
